Understanding End-to-end Encryption
Blockchain end-to-end encryption technology
An increasing need for privacy and security prompted people to devise ways of communicating through encrypted messages. With an end-to-end encryption communication mode, a person sends a message which the receiver only can read.
Essentially, no other person can read or modify the message apart from the sender and receiver of the information.
Here is how it works
A message such as “Hello Friend” is converted into a scrambled message which is incomprehensible to any person looking at it. For instance, “Hello Friend,” may look as follows:
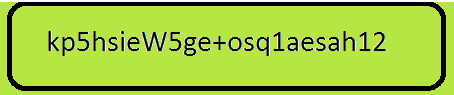
The process begins when an individual sends an encrypted message through the internet to another person. In return, the receiver gets the message through a gadget that receives electronic data, such as a computer or smart phone.
Like we have pointed out above, the message looks as:
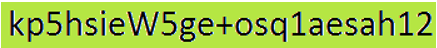
However, the recipient can convert it into readable message (Hello Friend) through decryption using a private key.
Private and public keys
As a fact, people use end-to-end encryption using public and private keys. However, these keys should relate to each other in order to send and receive a certain message. When we say they relate to each other, we mean that what the public key encrypts, the private key decrypts.
Public key: This is the key which you can share with any person. Whoever has it can send you encrypted information. It is similar to an email address, which you can give to anyone you wish to. With regards to cryptocurrencies, anyone with your public key or address can send you some coins or tokens.
In essence, each of these keys is a series of alphanumerical figures which are coined together.
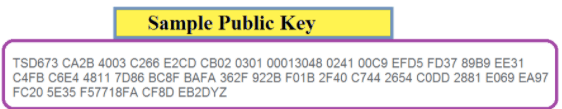
Private Key: This is the key which a person uses to access the information. As you note, it is unique to an individual. It is like your bank account PIN number or a password to an email address. Only the person with it can open the account and read the information which is there.

For instance, an individual can only access the contents in a cryptocurrency wallet, if he/she has a private key to the account. Therefore, for an individual to protect the information or data in an account, he/she needs to keep the private key safely. Unfortunately, if you lose your private key, you cannot access the contents of your account.
Example of end-to-end encryption
If Mariah wants to send an encrypted message to Joe, she takes Joe’s public key and encrypts her message. When Joe receives the message, he uses his private key to decrypt it. Through that simple process secure and private communication takes place between the two. No one can modify the message apart from the two individuals – sender and receiver.
Difference between public and private keys
There are several differences between a public and a private key.
- The private key is shared between the sender and the receiver only.
- Yet people can give the public key to anyone who needs it.
- The public key is used for encrypting a message while the private key is for decrypting it.
- The private key mechanism works faster than the private key.
Importance of end-to-end encryption
This modern means of communication has many benefits.
- It ensures high confidentiality since only the sender and receiver can access the information.
- The message remains authentic as no one can alter it apart from the sender and receiver.
- This increases the security of the information. For example, when hackers access your encrypted data, they cannot unencrypt it because they do not have the private key.
- The parties are protected from surveillance and eavesdropping.
Conclusion
Using end-to-end encryption enhances confidentiality, privacy, security and integrity. Surprisingly, the system is not as complicated as it seems. In this crypto world, people should learn to use encrypted messaging.






